Speed up compliance with EU CRA using PSA Certified components

In our series of posts, we have looked at several different methods device manufacturers can use to comply with EU CRA including self-assessment tools and third-party assessments. In this article, we learn about yet another different approach, IoT device manufacturers can use to comply with EU CRA and other global cybersecurity regulations using certified components. We explain how PSA Certified components like CPUs, SDKs, Operating Systems, and MCUs can speed up self-assessments and prove compliance to global cybersecurity regulations.
Objectives
The key objectives that we try to accomplish using this article:
- To help understand the fundamentals of PSA Certification.
- To explain how PSA Certification correlates with EU CRA requirements.
- To provide an overview of some of the different methods IoT device manufacturers can use to comply with EU CRA and other related cybersecurity regulations.
Target Audience
This article is focused on companies at the beginning of their cybersecurity journey or companies with a semi-established cybersecurity process, particularly manufacturers who create products with extensive software features.
We tru to keep the article less technical and make it especially useful to the following roles:
- Certification Managers: These roles are responsible for making sure the products that are developed goes through the cybersecurity regulation. They need to create and document clear evidence of compliance for their products.
- Product Managers and Business Owners: are constantly looking for simple and effective ways to clear regulations and take their product to the market quickly. Understanding how their product can piggyback on the cybersecurity certifications that components come with is crutial for these roles.
- Engineering and Project Managers: These roles are usually planning the different cybersecurity work including testing, vulnerability management, etc., that are needed for the product and hence need a clear understanding of what can be inherited and reused from the components they purchase and what needs to be created.
While this article provides a useful overview, this is just the starting point for technical roles like security engineers and software engineers. Technical engineers are expected to download the PSA Certified methodology document and evaluation checklist document to understand the certification in more depth.
The EU Cyber Resilience Act: A New Paradigm for IoT Security
The EU Cyber Resilience Act (CRA) is a landmark piece of legislation designed to bolster the cybersecurity of all products with digital elements sold within the European Union. The regulation’s scope is extensive, encompassing everything from individual microcontrollers and software libraries to finished consumer and industrial devices. It imposes a wide array of security mandates that span the entire product lifecycle. We have discussed the EU CRA in more detail in several of our past articles on the links here.
Key requirements of the CRA include:
Security by Design: Manufacturers must integrate security considerations into every phase of the product lifecycle, from initial design and development to end-of-life.
Vulnerability Management: Companies are required to have processes in place to identify, document, and remediate vulnerabilities in a timely manner.
Secure Updates: A crucial mandate is the provision of security updates for a period of at least five years, or for the expected lifetime of the product.
Transparency: Manufacturers must provide clear and comprehensive documentation regarding the security features of their products.
For many organizations, the CRA will necessitate a substantial evolution in their design methodologies, development practices, and post-market surveillance processes.
PSA Certified: A Framework for Building Trustworthy Devices
PSA Certified is a global partnership of security-conscious technology companies that provides a comprehensive framework for securing connected devices. It is not a regulation itself, but rather a certification scheme that offers a clear, structured path to implementing robust security. The entire framework is based on ten fundamental security goals, which address aspects like unique device identification, secure boot, isolation, and secure updates. These goals align closely with the principles of the EU CRA and other major global regulations.
The 10 Security Goals of PSA Certified
PSA Certified is built around ten fundamental security goals that provide a framework for securing connected devices from the chip to the cloud.
Unique Identification: Every device must have a unique and immutable identity that cannot be cloned.
Secure Boot: The device must verify that all software is authentic and from the correct source before it is executed.
Security Lifecycle: The device must have a defined lifecycle state (e.g., development, production, end-of-life) that can be securely managed.
Attestation: The device must be able to provide evidence to prove its identity, hardware and software status, and lifecycle state to other services.
Secure Update: The device must support a mechanism to securely update its software, and all updates must be authenticated.
Anti-Rollback: The update mechanism must prevent an attacker from reverting the device to an older, potentially vulnerable version of the software.
Isolation: Critical security functions and data must be isolated from the rest of the system in a secure processing environment.
Interaction: Non-secure parts of the system must use secure services provided by the isolated, secure processing environment.
Secure Storage: The device’s Root of Trust must provide a way to securely store critical data, such as cryptographic keys.
Cryptographic & Trusted Services: The device must provide a full suite of cryptographic functions (like encryption and hashing) and other trusted services.
How PSA Certified Directly Maps to EU CRA Requirements
The most significant advantage for manufacturers is the direct alignment between PSA Certified and the EU CRA. The work required for CRA compliance can be substantially addressed by using components that are already PSA Certified.
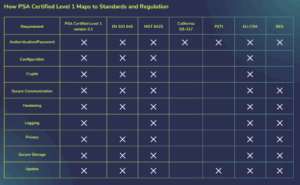
PSA Certified Level 1, for instance, has been updated to map directly to the essential requirements of the EU CRA. It also aligns with other key regulations, such as the UK’s Product Security and Telecommunications Infrastructure (PSTI) act and the US FCC Cyber Trust Mark. This mapping is not a coincidence; it is a deliberate effort by the PSA Certified consortium to provide a practical solution to a complex regulatory landscape.
By integrating a PSA Certified component—be it a microcontroller, a software development kit (SDK), or a full-fledged operating system—you inherit a significant portion of the security evidence required for your own product’s certification. This inheritance dramatically reduces the time, cost, and internal engineering effort needed to interpret and implement the complex legal and technical requirements of the CRA. Instead of starting from scratch, your team builds upon a foundation of proven, independently verified security.
It is crucial to understand that while certified components streamline compliance, they do not eliminate the final manufacturer’s responsibility. The manufacturer must ensure the component is integrated securely and that the overall product meets all regulatory requirements. The primary benefit is a massive reduction in the initial testing and documentation burden for that specific part of the system.
Example: We try to understand this concept using an imaginary example.
- Imaginary Company Name: Bright Nights Inc
- Imaginary Product type: Connected LED lamps
- Number of variants: 2; Lamp with Wi-Fi connectivity (connected to power), LED lamp with Bluetooth connectivity only (powered by batteries)
- MCU used in the device: ESP32-C6 for the Wi-Fi connected lamp, nRF54L15 for the BLE-only variant
Both variants of this device are impacted by the CRA and fall under the Default category of CRA.
ESP32-C6 SoC from Espressif has a PSA Certified Level 2 protection. The nRF54L15 SoC has a better security level. It comes with PSA Certified Level 3 protection. Both variants of the lamp can inherit security certifications from the corresponding underlying MCUs. The manufacturer, Bright Nights, just needs to provide evidence that their engineers have properly turned on the functionality available in the certified SoC properly as per the chipset vendor documentation. This works perfectly for requirements like secure updates, secure code execution and secure data storage. PSA Certified SoCs usually come with a RoT based bootloader, Trusted Execurtion Environments and Secure Key storage mechanisms which easily satisfy these requirements.
While creating the self-assessment technical documentation for CRA compliance, the manufacturer can simply provide proof of enabling the feature and testing it on a system level.
How the PSA certification works with other CRA compliance tools
The example of Bright Nights Inc, was too simple in terms of cybersecurity requirements. Most real-world devices have much more complex functionality than just on and off. There are more security requirements in devices with complex functionality but still falling into the default category of CRA. A connected refrigerator usually has a display panel and might need its users to authenticate themselves before they can change the settings of device. Software features, like authentication, need to be implemented and documented by the device manufacturers themselves. Those requirements can not usually be inherited by the PSA certification of the MCU components.
This is where a combination of PSA certified and self-assessment CRA tools come in handy. We have covered extensively about CRACoWi, CRA-AI and OCCTET in our previous posts. An AI-powered tool combined with component-level certifications can greatly speed up self-declaration assessments for EU CRA. We believe that, CRA-AI or OCCTET might be good tools to work with while inheriting component level certifications. Besides PSA Certified, we know that NXP Semiconductors uses and promotes SESIP for CRA compliance on component-level. We know that SESIP is also working on providing mappings between the SESIP certification and different regulatory standards.
With the number of automation tools and other options available for CRA compliance, companies that are aware of the different options available and know how to combine them to make good use of them will easily and cheaply clear the EU CRA regulation.
Further Reading
PSA Certified’s whitepaper that explains their mapping to different regulations https://www.psacertified.org/app/uploads/2024/10/PSA_Certified_Regulations_Whitepaper_Oct_2024.pdf