Best WiFi MCU for Upcoming Cybersecurity Regulations: NXP vs ESP32 vs STM32 WiFi

For product and engineering managers in the IoT space, the landscape is in constant motion. Yet, two acronyms are solidifying into the bedrock of future market access: the EU’s Cyber Resilience Act (CRA) and the US Cyber Trust Mark (CTM). While the CTM is slated as a “voluntary” program, viewing it as optional is a strategic mistake that could cost your products market share and brand reputation. This guide will explain why your team needs to be designing for CTM and CRA compliance today, how it synergizes with your existing CRA efforts, and why the single most important decision you can make to de-risk your next product launch is choosing the right Wi-Fi MCU. We will also compare the most popular Wi-Fi MCUs in the market to identify the best Wi-Fi MCU with the CRA and CTM in mind. The comparison focuses on NXP Semiconductors against the ESP32 series of SoCs from Espressif Systems and the STM32 series of WiFi modules from STMicroElectronics.
Why You Must Start Acting Before the Rules are Final
A common refrain from leadership might be, “Why invest in compliance for a program that isn’t even fully defined?” For managers overseeing IoT product development, the answer lies in your own project timelines.
The typical design cycle for a new connected product is notoriously long. A device slated for a market launch in the second half of 2026 is having its core architecture and component selection decided right now, in the latter half of 2025. The decisions you make today—the MCU you select, the security architecture you define—will be locked in for the life of that product.
That product will likely see its peak sales in 2027 and 2028. By that time, the US Cyber Trust Mark will be fully operational and the EU’s CRA will be mandatory. The grace periods will have expired, and the market will have clear expectations. Designing a product today without a clear path to CTM and CRA compliance is like setting sail into a storm without a compass. You are building in future risk, and costly re-designs.
Why CTM Compliance will not be “voluntary” for too long
While the FCC has positioned the Cyber Trust Mark as a voluntary program, market dynamics will quickly render it essential. Imagine browsing for a smart plug or a baby monitor on Amazon or Best Buy in 2027. At the top of the search filter sidebar, alongside “Brand” and “Price,” you might see a new checkbox: “Cyber Trust Mark Certified.”
Which products do you think consumers will choose? The ones with a clear, government-backed logo signifying they meet robust cybersecurity standards, or the ones left out?
This is not a far-fetched scenario. Retailers have a massive incentive to promote secure products. It reduces their own liability, minimizes customer complaints and returns related to security incidents, and protects their brand reputation. The CTM logo will become a powerful purchasing heuristic for consumers, and a critical filter for online visibility. Non-participation won’t be an option for any brand that wants to be seen, let alone sold.
How CRA Preparation Gives You a Head Start on CTM
As we have detailed in our previous article, Cyber Trust Mark After CRA, the work you do for the mandatory EU CRA directly prepares you for the US CTM. Both initiatives are built upon the same foundational security principles, largely derived from standards like NISTIR 8425 and ETSI EN 303 645. They both demand:
Secure by Design: Building security into the product from the ground up.
Vulnerability Management: Having processes to receive, assess, and patch vulnerabilities.
Secure Updates: Ensuring the integrity and authenticity of firmware updates.
Data Protection: Protecting sensitive data both on the device and in transit.
Secure Defaults: Shipping products with strong, unique passwords and secure configurations.
If your product development lifecycle is already being re-engineered to meet the rigorous, mandatory demands of the CRA, you have already done 90% of the work required for the CTM.
However, there is a key difference that presents a significant challenge: mandatory in-lab testing. The CTM program will require products to be tested and verified by accredited third-party labs. This is a potential bottleneck that can add significant time, cost, and risk to your product launch. Imagine failing a lab test late in the development cycle. The resulting delays and engineering costs could be catastrophic for a product’s business case.
This is where component selection becomes your most powerful tool for risk mitigation.
De-Risking Your Launch: The Power of a Pre-Certified MCU
The heart of any IoT device is its microcontroller unit (MCU). The MCU runs the core logic, manages the peripherals, and, most importantly, is the root of the device’s security.
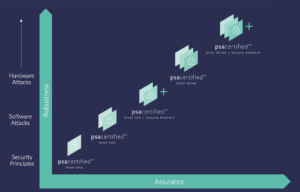
To navigate the CTM’s in-lab testing requirement, the smartest strategy is to build your device around an MCU that has already undergone rigorous, independent, third-party security evaluation. This is where PSA Certified Level 3 becomes the gold standard for managers looking to de-risk their projects.
Why is PSA Certified Level 3 so important?
PSA Certified Level 3 demonstrates protection against substantial physical and software attacks. Crucially, it requires a product to pass independent laboratory penetration testing. An MCU with this certification has already had its security claims validated by experts in a lab environment.
By choosing a PSA Certified Level 3 Wi-Fi MCU, you are essentially inheriting a vast amount of security work and, most critically, pre-vetted evidence that your device’s core is robust enough to pass CTM testing. You can walk into the CTM lab with a certificate that says the heart of your product is already a fortress.
Choosing the Best Wi-Fi MCU for 2026 and Beyond
Our research has identified two leading contenders in the Wi-Fi space that have achieved the coveted PSA Certified Level 3, making them prime candidates for your next CTM-compliant product.
Contender 1: NXP RW61x Series (RW612 & RW610)
The NXP RW61x series is a purpose-built family of MCUs designed for the new era of IoT security regulations. It is a multi-protocol powerhouse, integrating Wi-Fi 6, Bluetooth Low Energy 5.3, and 802.15.4 for Matter/Thread, all on a single chip.
Explicit Certification: The NXP RW61x is explicitly listed on the PSA Certified website. This is unambiguous, verifiable proof of its Level 3 status.
Key Security Features:
EdgeLock® Secure Enclave: The RW61x features a hardware-based secure enclave, a self-contained security subsystem that acts as a root of trust. It handles secure boot, key management, and cryptographic acceleration, isolating them from the main application processor.
Dual Certification: In addition to PSA Certified Level 3, the RW612 variant also boasts SESIP Level 3 certification. This makes it an incredibly efficient choice for companies targeting both the US and EU markets.
Contender 2: STMicroelectronics ST67W Series
The ST67W series is a new line of Wi-Fi 6 and Bluetooth LE wireless coprocessor modules from STMicroelectronics, developed in collaboration with Qualcomm. These modules are designed to be integrated with an external STM32 MCU, acting as a dedicated connectivity solution.
Explicit Certification: The ST67W61xM Series is explicitly PSA Certified Level 1, as confirmed by STMicroelectronics and the PSA Certified website.
Security Features: The module includes integrated hardware cryptographic acceleration, secure boot, and secure debug capabilities.
Contender 3: Espressif ESP32-C6
Espressif has become a dominant force in the IoT world, known for providing powerful, cost-effective, and highly integrated solutions. The ESP32-C6 is their first Wi-Fi 6 capable SoC and represents a major step forward in their commitment to security.
Certification: The ESP32-C6 SoC is PSA Certified Level 2, which means its core software and security architecture have been independently evaluated for vulnerabilities by a third-party lab.
Security Features: The ESP32-C6 comes equipped with a robust set of security hardware, including Secure Boot, Flash Encryption, a Digital Signature Peripheral, and cryptographic accelerators.
The Verdict: NXP WiFi vs STM32 WiFi vs ESP32 WiFi for US CTM
The choice between these components is a classic strategic decision about risk, cost, and allocation of engineering resources.
The STMicroelectronics ST67W (Level 1) is a strong foundational choice. It comes from a leading vendor and provides a clear, documented set of security features. For teams that already have deep security expertise and a budget for extensive third-party testing, this module allows them to pair a capable radio with a powerful host MCU of their choice. The risk here is that the burden of proof for security effectiveness is on you. The PSA L1 certificate is the starting line, not the finish line.
The Espressif ESP32-C6 (Level 2) is a decent choice for de-risking a project. The independent, third-party validation against software attacks is a massive advantage. It provides a verifiable answer to the question, “How do you know your core is secure?” This can save invaluable time and money by reducing the scope of pre-certification testing your team needs to perform. For a manager, this means a bit more predictable timeline and budget on the path to CTM certification.
The NXP Semiconductor RW61x series of SoCs (Level 3) are the best choice for derisking a project. PSA Certified Level 3 demonstrates protection against substantial physical and software attacks. Crucially, it requires a product to pass independent laboratory penetration testing. An MCU with this certification has already had its security claims validated by experts in tough lab environments.
By choosing a PSA Certified Level 3 Wi-Fi MCU, you are essentially inheriting a vast amount of security work and, most critically, pre-vetted evidence that your device’s core is robust enough to pass CTM testing. You can walk into the CTM lab with confidence that the heart of your product is already a fortress. For the specific goal of minimizing risk and maximizing compliance efficiency for both US and EU markets, the NXP RW61x series is the clear winner.
Explore the Full US Cyber Trust Mark Series
This article is part of our deep-dive cluster on the US Cyber Trust Mark. Read our entire coverage here. Want to know more about how to use certified components to get the CRA and CTM labels? Read our articles on PSA Certified for CTM, PSA Certified for CRA, and SESIP for CRA.
Get Expert Analysis in Your Feed
Follow us on LinkedIn for more future articles: https://www.linkedin.com/company/iot-regulations/.