How to get the US FCC Cyber Trust Mark using PSA Certified MCUs and NIST 8425
The landscape of IoT security is undergoing some major changes with some governments, like the EU, bringing mandatory cybersecurity regulations while others, like Singapore, have introduced voluntary schemes combined with educating the consumer. The United States has taken the latter approach and introduced the US Cyber Trust Mark (CTM) program. We have already created introductory articles on the CTM and the requirements of NIST 8425 (IoT Device Cybersecurity Capability Core Baseline) that have been chosen as the guiding principle for this program. However, a lot of the commercially sold MCUs, that form the heart of today’s consumer IoT devices, come with PSA Certification. In this article we look at how device manufacturers can get the US Cyber Trust Mark PSA Certification easily by inheriting the certification in PSA Certified MCUs and NIST 8425.
Target Audience
High-Level Overview of PSA Certified Levels
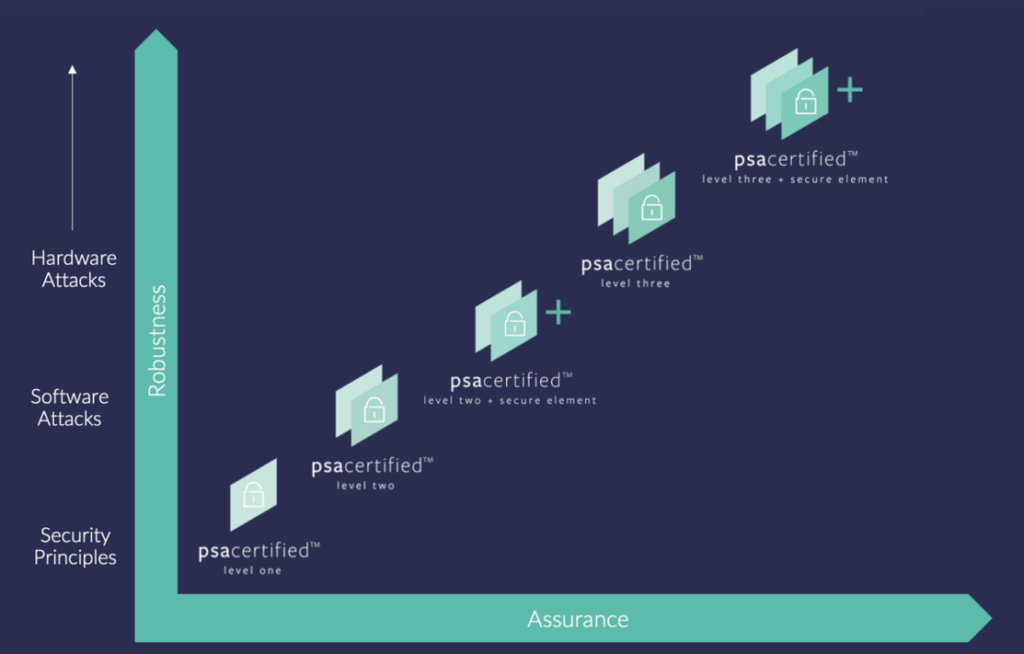
PSA Certified is a multi-level security assurance scheme that provides a common language and framework for securing connected devices.
PSA Certified Level 1: This is a foundational level based on a structured questionnaire. Developers assess their device against the 10 security goals of the PSA Security Model, ensuring best practices in hardware and software design have been followed. It’s main goal is to establish a secure design philosophy.
PSA Certified Level 2: This level moves from documentation to independent validation. A third-party security laboratory performs test on the device’s Root of Trust (RoT). The lab’s goal is to break the security using scalable software attacks. A successful Level 2 certification provides tangible evidence that the chip’s foundational security is robust against remote attackers.
PSA Certified Level 3: This is a high level of assurance, targeting devices that may face significant physical threats. It includes all the testing of Level 2, plus advanced, time-boxed hardware attacks, such as side-channel analysis and fault injection, to try and extract secrets directly from the silicon.
PSA Certified Level 4: A specialized track for devices with high-value cryptographic assets, like SIMs, iSIMs, or Secure Elements. It involves intensive evaluation against state-of-the-art physical attacks, ensuring the core secrets are protected even from well-funded attackers.
NIST 8425 requirements
The NIST 8425 takes a system level definition of what a product is. For example, a smart thermostat is an “IoT device“. But NIST 8425 defines the “IoT product” as the combination of the connected thermostat, the mobile application and the cloud backend application that controls all of this. The requirements in NIST 8425 can be categorized into three fundamental categories:
Device-Level Requirements: These are the foundational, immutable security capabilities baked into the device’s hardware and core firmware. They concern the device’s ability to protect itself and its most critical secrets. Think of this as the security of the silicon’s Root of Trust (RoT).
Product-Level Requirements: This category covers the assembled product that a consumer buys and interacts with. It’s about how the device behaves as a whole, how it communicates securely, and how it presents its features to the user and the cloud. These requirements are built upon the device-level foundation.
Process-Level Requirements: This layer extends beyond the technology itself to the manufacturer’s operational policies and promises. It includes how the manufacturer handles vulnerability reports, guarantees the availability of security updates, and manages user data.
Meeting the Mandates Part 1: Device-Level Requirements
These are the core requirements for the device to protect itself. A PSA Certified MCU provides pre-verified solutions to these challenges.
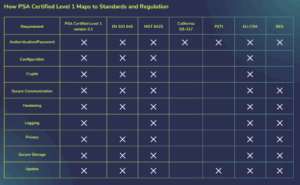
| Device-Level Requirements | The Device’s Responsibility (The “What”) | How PSA Certified Provides a Verifiable Solution (The “How”) |
| Device Identification | The IoT device must possess a unique, unalterable identity. | The PSA Root of Trust (PSA-RoT) contains an immutable Unique ID or Hardware Unique Key (HUK), proven by lab testing to be resistant to software modification. |
| Data Protection (at Rest) | The device must protect the confidentiality and integrity of sensitive data stored on the device (e.g., keys, credentials). | The PSA Protected Storage API is used to store secrets. It leverages the RoT to encrypt data and bind it to the specific device, protecting it even if flash memory is read out. |
| Secure Software/Firmware Updates | The device must verify the authenticity and integrity of any new software before installing it and prevent rollbacks to vulnerable versions. | The PSA-RoT’s Secure Boot process, using the PSA Crypto API, is capable of verifying the digital signature of firmware. PSA Certified Level 2 MCUs are explicitly tested by certification labs to bypass this. |
| Logical Access to Interfaces | The device must control access to local and network interfaces. Access to some interfaces must be available only upon proper authentication and authorizations. | While NIST doesn’t mandate how this must be implemented, it is common practice to implement authentication controls using the PSA Certified Crypto API to make the implementation. Any access control (e.g., a password check) is useless if it can be bypassed. PSA Certified enables a robust solution by running the authentication logic in the isolated Secure Processing Environment (SPE), making it non-bypassable by the main OS. |
Meeting the Mandates Part 2: The Product-Level Requirements
For an “IoT Product” to be secure, the device must be a trustworthy participant. This means it has responsibilities that extend beyond its own physical hardware.
| Product-Level Requirements | The Device’s Responsibility (The “What”) | How PSA Certified Enables Trust (The “How”) |
| Secure Communication | The IoT device must be able to protect data in transit by implementing a robust and secure communication protocol like TLS. | A TLS connection is only as strong as its private key and certificates. The device uses PSA Protected Storage to secure these keys and certificates within the RoT, preventing it from being stolen and used to impersonate the device. PSA Certified also enables a robust solution by running the key negotiation logic in the isolated Secure Processing Environment (SPE) |
| Cybersecurity State Awareness | The IoT device must be able to report its internal security state (e.g., software version, failed login attempts) to the system in a way that can be trusted. | Generating internal logs of the system state is mostly related to good software development. However, these logs must not be modifiable by any bad actors in the system. The device can create a signed, unforgeable “report card” of its state using the PSA Attestation API. The cloud can trust this report because it is signed by a hardware-protected key that any malware cannot access. |
| Secure Interaction & Command Handling | The IoT device must be able to authenticate the source of all incoming commands and prove that critical actions were taken upon receiving the command. | The device runs command verification logic inside the SPE. After executing a command, it can use PSA Attestation to provide a non-repudiable receipt to the cloud, confirming the action was completed by a genuine, uncompromised device. |
| Full Lifecycle Management | The IoT device must support secure onboarding into the system and provide a mechanism for secure data erasure at its end-of-life. | The Unique ID and an initial Attestation Token provide trust for onboarding. For decommissioning, a trusted function in the SPE can use the PSA Protected Storage API to securely wipe all secrets, preventing data leakage from discarded devices. |
All the device level and product level requirements in NIST 8425 can easily be met by using PSA Certified features in the MCU. The PSA Certified APIs are available for all PSA Certified MCUs and are well integrated into popular RTOS like FreeRTOS and Zephyr OS and maintained by ARM. The process related requirements like vulnerability handling, product documentation around secure usage and support period are related to the security policies in an organization and outside the scope of this article.
Which PSA Certified level for the US Cyber Trust Mark?
The US Cyber Trust Mark will require evaluation by an authorized, third-party test laboratory. This is where building on a PSA Certified component becomes a powerful strategy. By choosing PSA Certified Level 2 or higher MCUs, you are building on a foundation that has already passed an independent lab evaluation covering the core requirements of NIST IR 8425. PSA Certified significantly reduces the effort needed by developers to comply with these regulations.
The test methodology for the CertLabs is still work in progress by the FCC. Through the principle of composition, the CertLabs may reuse this existing certification. This dramatically reduces the scope, cost, and risk of your final product evaluation, allowing you to focus on the security of your application layer.
In today’s regulatory environment, security is not just a feature; it is the foundation. By understanding the device’s dual role—protecting itself and acting as a trusted citizen in a larger system—and by leveraging frameworks like PSA Certified, developers can easily build the secure, compliant, and trustworthy products and claim the US Cyber Trust Mark.